Our
News
Top 5 Cyber Threats to Business
Top 5 Cyber Threats to Business With the ever-growing digital age, cyber crime is on a constant rise, and no one seems to be quite safe-- especially small businesses. Small businesses seem to be the...
Cyber’s Gender Gap
Cyber's Gender Gap Cybersecurity and Information Technology holds a reputation for being a field of study continuously dominated by men. In 2021, women made up roughly 20-24% of the cybersecurity...
Supply Chain Vulnerabilities and TPRM
Supply Chain Vulnerabilities and TPRM Supply chain management and Third Party Risk Management (TPRM). Is there a difference? Companies often don't realize how frequently security breaches happen...
The Evolution of Cyber Attacks in 2022
The Evolution of Cyber Attacks in 2022 As we celebrate the arrival of another new year, we must also prepare for what lies in store for us the following 12 months. As time goes on, cybersecurity...
Existing CMMC to CMMC 2.0 Mapping
It is known throughout the defense industries that the CMMC 2.0 requirements are going to be in effect. For those of you who built your documentation mapped to the original requirements here are...
Cyber Tips for Remote Employees
Cyber Tips for Remote Employees Cyber Security Awareness Month may be over, but protection should last all year long! Nothing is scarier than a breach in your security or information. As a company,...
6 Cyber Security Shopping Tips
6 Cyber Security Shopping Tips As the holidays approach, so do the gift deadlines. As everyone scrambles to their favorite shopping websites for the holidays, people often favor the convenience of...
Top 5 Data Breaches in History
Top 5 Data Breaches in History If you work in cyber security, chances are you are at least familiar with what CMMC is. The Cybersecurity Maturity Model Certification (CMMC) is intended to serve...
Facebook, Instagram, and WhatsApp were down– Here’s what we Know
Remote Work is Leaving Us More Vulnerable to Cyber Attacks-- Here's Why. Since the COVID-19 Pandemic first hit, workers were sent home by the thousands to begin the now-popular "remote work". What...
Women in the Cyber Field
Women in the Cyber Field Cyber security is without a doubt a lucrative career choice. Good money, good benefits, job security, so why are so few women joining the field? These gender differences are...
10 Cybersecurity Myths we Should Stop Believing
10 Cybersecurity Myths we Should Stop Believing Cyber criminals aren't just out to get the big companies. If you own a mobile device, chances are you are a target of cyber attack. Over the...
5 Things to Prepare you for CMMC
5 Things to Prepare you for CMMC If you work in cyber security, chances are you are at least familiar with what CMMC is. The Cybersecurity Maturity Model Certification (CMMC) is intended to serve...
5 Ways to Improve your Mobile Security
Five Ways to Improve your Mobile Security Cellphones, while our biggest blessing, is also our biggest curse. Worlds of knowledge at our fingertips, online banking, shopping, and everything that...
Remote Work is Leaving Us More Vulnerable to Cyber Attacks– Here’s Why.
Remote Work is Leaving Us More Vulnerable to Cyber Attacks-- Here's Why. Since the COVID-19 Pandemic first hit, workers were sent home by the thousands to begin the now-popular "remote work". What...
T-Mobile Data Breach Said to Have Impacted over 40 Million People
Hackers Leave Over 40 Million T-Mobile Customers, Past and Present, Exposed T-Mobile, the mobile telecommunications company, recently suffered one of the largest data breaches in company history....
Top 5 Devastating Viruses
Top 5 Devastating Viruses Viruses have been around almost as long as having computers in the home. Over the years, countless viruses, ransomware, and the like have been released into the cyber...
10 Exploited Vulnerabilities in Cybersecurity
10 Exploited Vulnerabilities in Cybersecurity The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the broader U.S Government are providing...
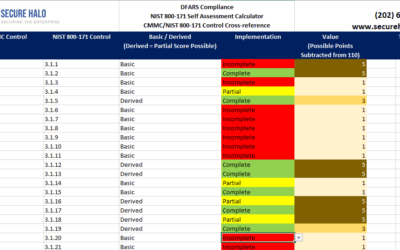
DFARS Compliance – NIST 800-171 SPRS Self Assessment Calculator
With the implementation of the DFARS Cybersecurity requirements that went into effect on November 30, 2020. A self-assessment score is required to be submitted to the DOD Supplier Performance Risk...