Cybersecurity News
Top 5 Cyber Threats to Business
Top 5 Cyber Threats to Business With the ever-growing digital age, cyber crime is on a constant rise, and no one seems to be quite safe-- especially...
Cyber’s Gender Gap
Cyber's Gender Gap Cybersecurity and Information Technology holds a reputation for being a field of study continuously dominated by men. In...
Supply Chain Vulnerabilities and TPRM
Supply Chain Vulnerabilities and TPRM Supply chain management and Third Party Risk Management (TPRM). Is there a difference? Companies often don't...
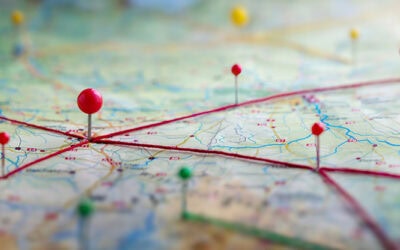
The Evolution of Cyber Attacks in 2022
The Evolution of Cyber Attacks in 2022 As we celebrate the arrival of another new year, we must also prepare for what lies in store for us the...
Existing CMMC to CMMC 2.0 Mapping
It is known throughout the defense industries that the CMMC 2.0 requirements are going to be in effect. For those of you who built your...
Cyber Tips for Remote Employees
Cyber Tips for Remote Employees Cyber Security Awareness Month may be over, but protection should last all year long! Nothing is scarier than a...
6 Cyber Security Shopping Tips
6 Cyber Security Shopping Tips As the holidays approach, so do the gift deadlines. As everyone scrambles to their favorite shopping websites for...
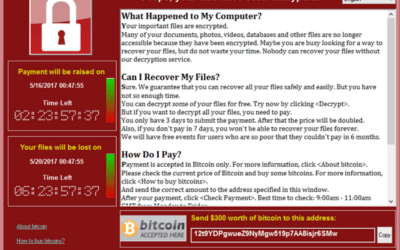
Top 5 Data Breaches in History
Top 5 Data Breaches in History If you work in cyber security, chances are you are at least familiar with what CMMC is. The Cybersecurity Maturity...
Facebook, Instagram, and WhatsApp were down– Here’s what we Know
Remote Work is Leaving Us More Vulnerable to Cyber Attacks-- Here's Why. Since the COVID-19 Pandemic first hit, workers were sent home by the...
Women in the Cyber Field
Women in the Cyber Field Cyber security is without a doubt a lucrative career choice. Good money, good benefits, job security, so why are so few...
10 Cybersecurity Myths we Should Stop Believing
10 Cybersecurity Myths we Should Stop Believing Cyber criminals aren't just out to get the big companies. If you own a mobile device, chances...
5 Things to Prepare you for CMMC
5 Things to Prepare you for CMMC If you work in cyber security, chances are you are at least familiar with what CMMC is. The Cybersecurity Maturity...
5 Ways to Improve your Mobile Security
Five Ways to Improve your Mobile Security Cellphones, while our biggest blessing, is also our biggest curse. Worlds of knowledge at our fingertips,...
Remote Work is Leaving Us More Vulnerable to Cyber Attacks– Here’s Why.
Remote Work is Leaving Us More Vulnerable to Cyber Attacks-- Here's Why. Since the COVID-19 Pandemic first hit, workers were sent home by the...
T-Mobile Data Breach Said to Have Impacted over 40 Million People
Hackers Leave Over 40 Million T-Mobile Customers, Past and Present, Exposed T-Mobile, the mobile telecommunications company, recently suffered one...
Top 5 Devastating Viruses
Top 5 Devastating Viruses Viruses have been around almost as long as having computers in the home. Over the years, countless viruses, ransomware,...
10 Exploited Vulnerabilities in Cybersecurity
10 Exploited Vulnerabilities in Cybersecurity The Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation...
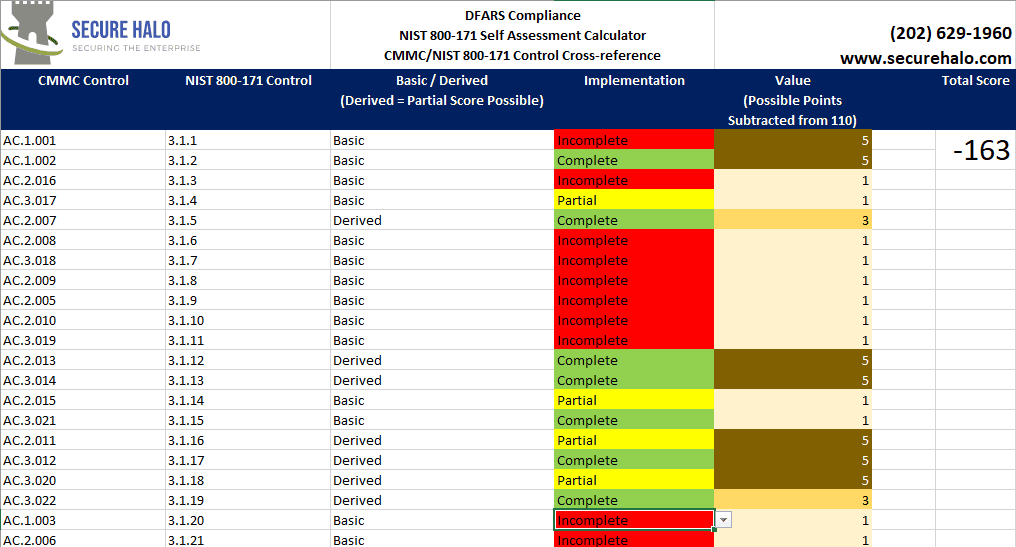
DFARS Compliance – NIST 800-171 SPRS Self Assessment Calculator
With the implementation of the DFARS Cybersecurity requirements that went into effect on November 30, 2020. A self-assessment score is required to...
Cyber Due Diligence Prevents Private Equity, M&A Disasters
Would you value a potential investment or acquisition target differently if you knew that it had been breached or was at high risk for cyber losses?...
Just Weeks to Meet NYDFS Third-Party Deadline
The final, and many would say most onerous, phase of the New York Department of Financial Services (NYDFS) Cybersecurity Regulations goes into...
Infographic: 5 Resolutions to Improve Cybersecurity Right Now
Making cyber risk management plans for 2019? The experts at CyberFortis, the financial services division of Secure Halo™, offer five steps every...
Secure Halo™ Announces Social Engineering Workshop
Free Oct 16 Event Highlights Cybersecurity Awareness Month and DC CyberWeek Silver Spring, MD — Secure Halo™ today announced it will hold a...
Beyond Compliance: Making Security a Business Strategy
White Paper - Beyond Compliance Corporations of all sizes are awash in regulatory requirements, including a growing number related to data security...
NYDFS September 3 Deadline – Are You Ready?
September 3 marks the next critical deadline for companies covered by the cybersecurity regulations (23 NYCRR Part 500) set forth by the New York...
Secure Halo™ a Third-Time Cybersecurity Awareness Month Champion
Silver Spring, MD — Secure Halo™ today announced that it has become a third-year Champion of National Cybersecurity Awareness Month (NCSAM) 2018. It...
New York’s Cybersecurity Regulations: One Year into Implementation
It has been almost a year since the New York State Department of Financial Services (NYDFS) Cybersecurity Regulation’s first transitional deadlines...
Addressing Third-Party Security Risks
IT Business Edge published an article on "Addressing Third-Party Security Risks," in which Will Durkee, Director of Security Solutions for Secure...
Security Ratings and Assessments – Why Together They Achieve Better Enterprise Health
White Paper - Security Ratings and Assessments Resource-conscious risk and IT professionals may turn to security ratings which scan from the outside...
Insider Threat: It’s Real and It’s Costly
Automotive maker Tesla’s allegation this week that a former employee wrote software that hacked company systems and leaked confidential information...
Improve Your Third-Party Risk Management Program in Four Steps
News continues to break on organizations facing fines, data loss, and shutdowns due to a lack of due diligence in their vendor selection process and...
Get In Touch
962 Wayne Ave, #310
Silver Spring, MD 20910
(301) 304-1700 (Sales)
(202) 629-1960 (Office)
info@securehalo.com