
by TSC Newsroom | Jun 28, 2017 | Blog
In addition to setting up appropriate defensive measures to keep intruders out, having an incident response plan established in case a ransomware attack or a breach does happen is essential. Each member of your team should know exactly what they have to do in response...
by Richard Osborne | Jun 7, 2017 | Blog
Just as Thomas Friedman’s best seller, The World is Flat, tackled the complex forces reshaping modern political economy, Wannacry is reshaping cyber risk management for the digital economy. Destructive powers, once the preserve of a few nation states, are now...

by Richard Osborne | May 18, 2017 | Blog
Cyberspace is defined as “the notional environment in which communication over computer networks occurs.” This formerly applied only to computers, but with rapidly evolving technology, it now applies to anything with an operating system. We have come a long way since...

by TSC Newsroom | May 16, 2017 | Blog
The presence of physical security in the form of gates and guards offers false hope to companies looking to protect their sensitive data. An effective security posture requires much more than physical security and/or legacy preventative controls, such as firewalls...
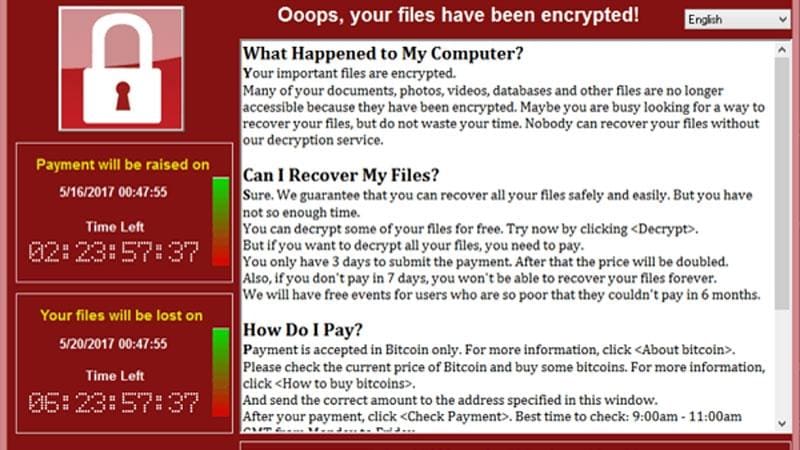
by TSC Newsroom | May 15, 2017 | Blog
A ransomware attack spread throughout the world over the weekend, infecting systems in 150 countries and counting. The attack, known as “WannaCry,” used software code stolen from the National Security Agency that was posted online. No industry was unscathed as...
by Richard Osborne | May 8, 2017 | Blog
Outsourcing network services is a common business practice for most large companies. From communication service providers to manufacturing facilities as well as healthcare or financial service providers, outsourcing is an effective way to reduce overall cost of...







