Top 5 Devastating Viruses
Viruses have been around almost as long as having computers in the home. Over the years, countless viruses, ransomware, and the like have been released into the cyber world, but few have been as impactful and devastating as the ones listed here. In this blog, “devastation” is counted as overall impact and cost to recover.
5) WannaCry
Cost of damages: $4 Billion
Type of Attack: Ransomware
Released in 2017, WannaCry is the most famous of ransomware attacks. WannaCry infected 150 countries by taking over the computer and encrypting the user’s files, and demanding a bitcoin payment to retrieve the encrypted files. WannaCry hit approximately 200,000 computers globally including homes, businesses, and even governments. Computers with outdated software were especially hit hard, which is why it is recommended to keep your software patched and up-to-date.
4) ILOVEYOU
Cost of damages: $15 Billion
Type of Attack: Worm
Y2k was the beginning of a new era, and with it, came new threats. The “ILOVEYOU” virus spread rapidly under the guise of a fake love letter attachment delivered over email. Upon its sending, the worm would replicate and send itself to the victims entire contact list, continuing the . Shortly after its creation and release, it was spread to over 10 million computers. The creator, a college student lacking funds in the Philippines, reported that he initially created it to steal passwords of accounts he couldn’t afford to use. It was also reported that the creator had no idea just how devastating it would be.
3) Klez
Cost of damages: $19.8 Billion
Type of Attack: Worm
As we get into the top 3, we talk about the Klez virus. This virus spread so rapidly that it infected approximately 7.2% of all computers(~7 million PCs) in the year 2001. This worm was particularly advanced for the time, sending fake emails, spoofing recognized senders and, among other things, attempting to deactivate other viruses. A worm is a worm. It came in a various forms, each got increasingly deadly to the user. It infected the user’s files, and replicated itself to the victim’s network.
2) Sobig
Cost of damages: $30 Billion
Type of Attack: Worm
Another worm on this list, the Sobig virus. In 2003, this worm spread worldwide and dealt some severe damage. Several versions (named Sobig A-F) were released in close proximity, making the virus unrecognizable and unavoidable, with SobigF being the most devastating. This program disguised itself as legitimate computer software attached to emails. The creator was never found
1) MyDoom
Cost of damages: $38 Billion
Type of Attack: Worm
Mydoom is by far the worst computer virus to break out in history and hopefully, it stops here .his virus was released in 2004 and cause (in 2004 dollars) $38 billion in damages. Adjusting to 2021 dollars, it could equate to approximately $49 billion. At its height, Mydoom, also known as Novarg, was responsible for 25% of all emails sent. Like most worms on this list, email addresses are taken from the victim. However, unlike the other worms, it also roped those infected machines into a web of computers called a botnet that performed Distributed Denial of Service (DDoS) attacks. These attacks were intended to shut down a target website or server. Mydoom is still around today, making up about 1% of all phishing emails. That percentage may seem small, but it equates to about 1.2 billion copies each year, which emphasizes the importance of never clicking on an attachment you’re unsure of!
“Cyber security is a shared responsibility, and it boils down to this: in cybersecurity, the more systems we secure, the more secure we all are.”
Jeh Johnson
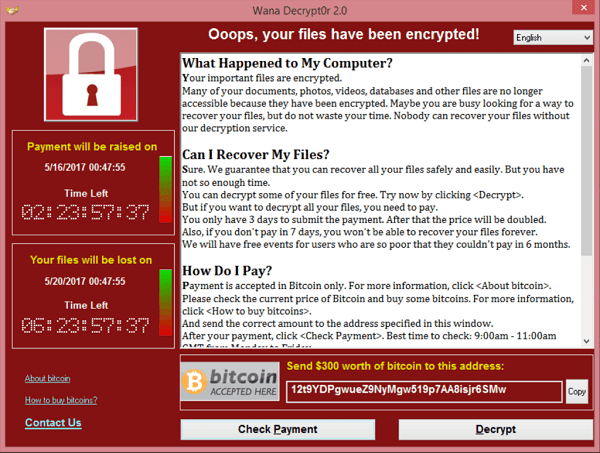


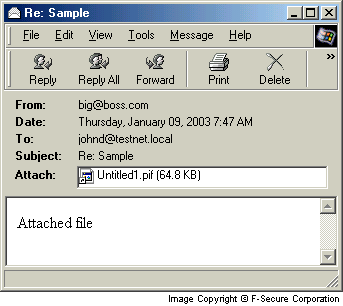

Screenshots of malware in action by descending order (WannaCry, ILOVEYOU, Klez, Sobig, MyDoom)
HOW SECURE HALO CAN HELP.
Stopping risks before they start!
Here at Secure Halo, we offer a variety of services. Third Party Risk Management is one of our specialties! With our TPRM services, we analyze the threats to your business before it’s too late. To learn more, click here.



