 Just as Thomas Friedman’s best seller, The World is Flat, tackled the complex forces reshaping modern political economy, Wannacry is reshaping cyber risk management for the digital economy. Destructive powers, once the preserve of a few nation states, are now possessed by ever diffuse state and non-state actors, including criminal organizations and hacktivists. More unmitigated and high risk actors have sophisticated tools at their disposal, making timely risk management no longer an ideal; it is an essential business function.
Just as Thomas Friedman’s best seller, The World is Flat, tackled the complex forces reshaping modern political economy, Wannacry is reshaping cyber risk management for the digital economy. Destructive powers, once the preserve of a few nation states, are now possessed by ever diffuse state and non-state actors, including criminal organizations and hacktivists. More unmitigated and high risk actors have sophisticated tools at their disposal, making timely risk management no longer an ideal; it is an essential business function.
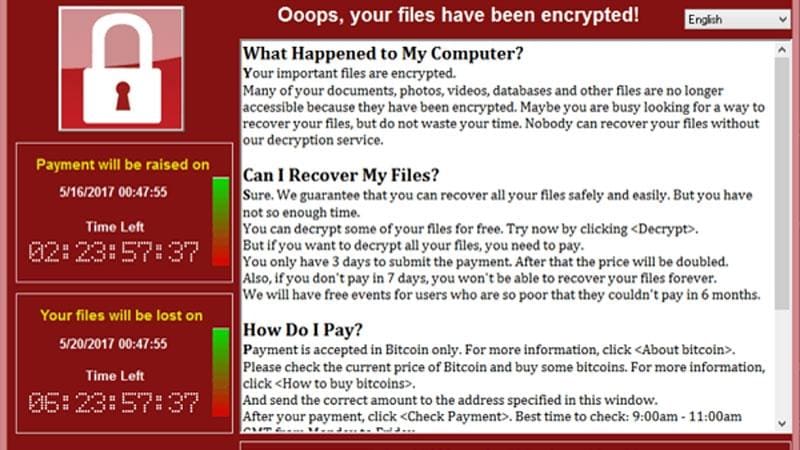
The Wannacry malware attacks, which infected an estimated 200,000 computers worldwide, provide another example of escalating and systemic cyber risk. Security analysts have found clues tying the massive ransomware attack to the Lazarus Group, linked to North Korea. Lazarus and North Korea are believed responsible for the 2016 attack for financial gain on banks using the SWIFT messaging network, and the 2016 attack on SONY for geopolitical purposes. The scope and scale of those attacks, were however, limited by North Korea’s infrastructure, capability and resources.
Hacking Goes Mainstream
With Wannacry, traditional risk calculus has been turned upside down. Analysts say that Wannacry bears signs of a cybercrime effort rather than a nation-state campaign. Sophisticated malware attacks are not exclusively used just by nation-states for intelligence purposes, or by well-financed criminal organizations. They are now deployed by unrestrained industrial scale criminal actors without regard to harm against civilians.
Wannacry spread using a program that had been leaked or stolen from the U.S. National Security Agency (NSA). The release of these tools can accelerate attacks on corporate systems in the window between their disclosure and the deployment of patches. As a result, proactive understanding of corporate assets is necessary, along with use of vulnerability management software to run scans and reports to ensure vulnerabilities are being mitigated. Similarly, business continuity and disaster recovery plans aren’t just interesting volumes for the bookshelf, but essential to accelerating and assuring a return to full operating capacity in the event of an attack.
In some cases, the Wannacry malware variants targeted legacy software no longer supported by vendors, such as Microsoft XP. This exposes companies (and consumers) to risk when their technology refresh rate is behind the vendors’ supported roadmap. Similar to a litany of other resource constraints impairing cyber security improvements, small and medium sized businesses (SMBs) are at a greater disadvantage than large enterprises. SMBs must take the time to assess critical and connected systems in accordance with vendor support programs. If the vendor has indicated it plans to stop supporting the solution used, proactively consider a replacement before its end-of-life. Due to the unprecedented nature of the Wannacry attack, Microsoft pivoted to develop a solution for an unsupported system – but it was not legally required to do so. For companies already infected, even this shining example of Microsoft’s corporate citizenship won’t unlock their damaged systems.
Wannacry is a warning shot, if you haven’t fallen victim to it. Don’t ignore the lessons it may teach you. You may believe that a sophisticated nation state has no interest in attacking your company, but indiscriminate criminals show no restraint and now carry bigger sticks.